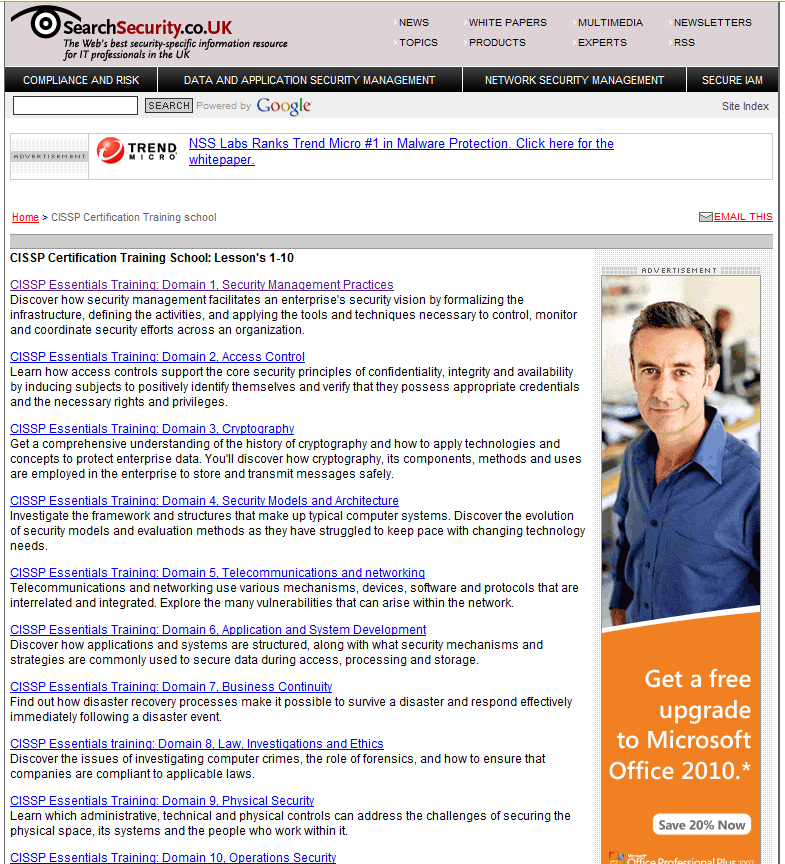
SearchSecurity.co.uk are looking to help out the Security Pro in these hard economic times. I assume this offer is open to anyone who has a SearchSecurity Account, or who signs up. So I guess its worth a punt.
Heres the info:
That’s why the editors of SearchSecurity.co.UK are offering this exclusive opportunity to participate in our complimentary CISSP Certification Training school. Simply activate your complimentary membership today and gain immediate access to these unique lessons,
including:
— CISSP Essentials Training: Domain 1, Security Management Practices
— CISSP Essentials Training: Domain 2, Access Control
— CISSP Essentials Training: Domain 3, Cryptography
— CISSP Essentials training: Domain 4, Security Models and Architecture
— CISSP Essentials Training: Domain 5, Telecommunications and networking
— CISSP Essentials Training: Domain 6, Application and System Development
— CISSP Essentials Training: Domain 7, Business Continuity
— CISSP Essentials Training: Domain 8, Law, Investigations and Ethics
— CISSP Essentials Training: Domain 9, Physical Security
— CISSP Essentials Training: Domain 10, Operations Security
Take advantage of this exclusive opportunity to participate in our complimentary CISSP Certification Training school, featuring security guru and president of Logical Security, Shon Harris. This is the perfect, free opportunity to increase your security intelligence and prepare for the CISSP exam. Don’t delay. Sign up for SearchSecurity.co.UK for complete access to these expert videos online now, while you have this email open!
http://go.techtarget.com/r/10068111/8974973