Since the beginning of the year I have jumped on the Apple bandwagon, and acquired a few of their lovely products. I like the look of them, I like how they work, but I am not the biggest fan of the cost 🙂 However, it obviously hasn’t stopped me becoming a fan. So with cost in mind, one thing that is of course a worry is losing my MacBook Pro, iPhone or other bit of kit. I looked at the Mobile Me offering, but I didn’t fancy paying Apple for more services, when I only wanted one feature. This is when I stumbled across Orbicle’s Undercover, its tracking software for Mac OSX and iOS (iPhone, iPod Touch, iPad). I contacted the guys in Belgium and they were kind enough to let me have a copy to review, so here we go.
I started off with the iPhone. As per usual you need to pop into the App Store, locate Undercover (a quick search soon takes you there) purchase and install. The first thing you will notice at this stage is the cost $4.99 (£3.37) that’s a good way to get started. Once you have installed the App you have to enter an email address that you will register the phone to, and an appropriate name for the device, you will then get a notification to expect an email to setup your Undercover account, you need this for device tracking, and to log into the web console.
Now we check the email and as promised, we have some verification to take care of.
Once we are all signed up we can login to the Undercover Web portal and manage our devices.
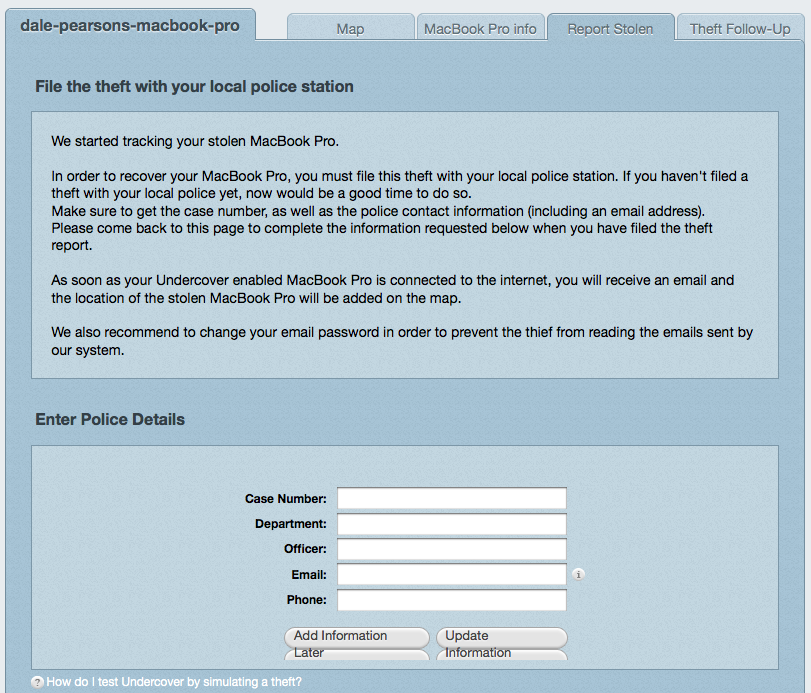
Once we are logged in we can instantly see where the iPhone is reported (using Wi-Fi positioning ,GPRS, or GSM Cell) to be (as the programming is running on the iPhone). We can get information on the iPhone (serial number, etc), we can then report it lost or stolen, and fill out police information, so we can create a nice bundled report to send to the police.
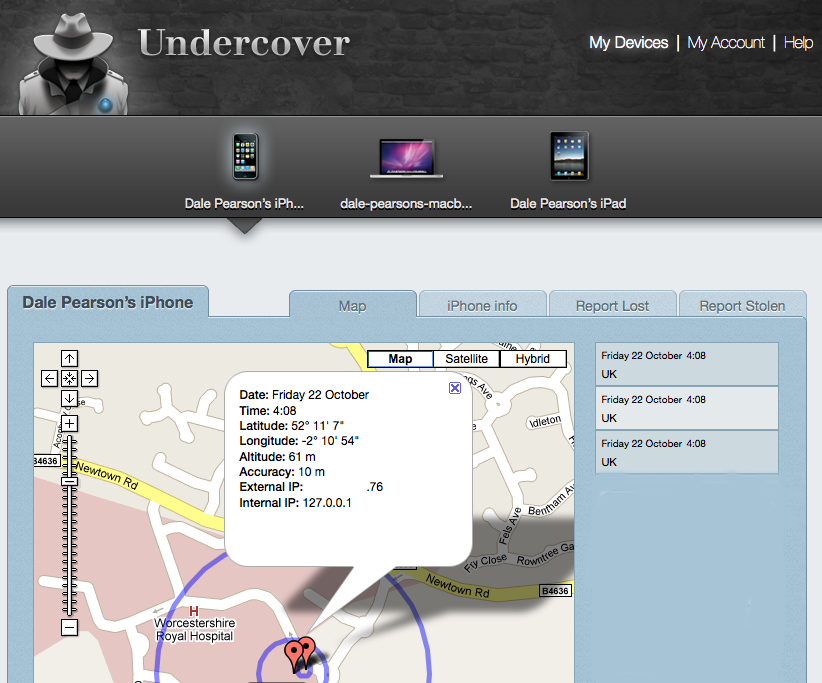
If we decide to do a test and decide our beloved iPhone is lost or stolen, we then have the ability to push an alert to the device.
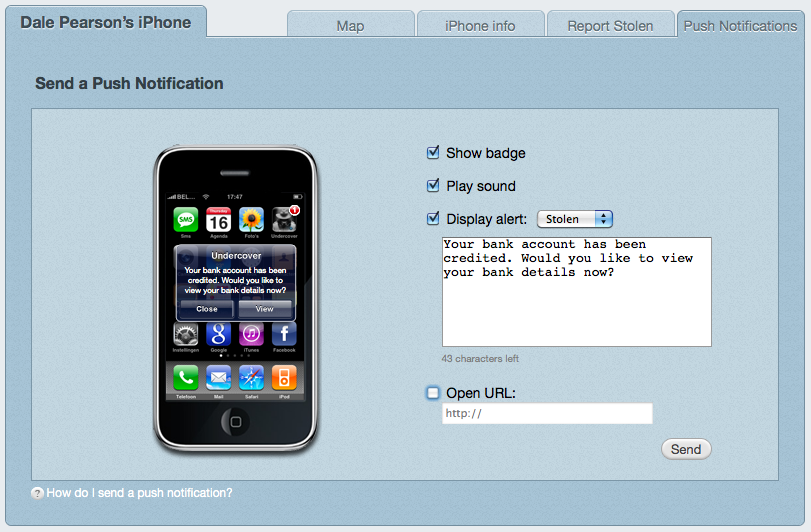
We can configure our own message, and even force the phone to go to a specific website. Once we press send, just moments later we get the alert on the phone.
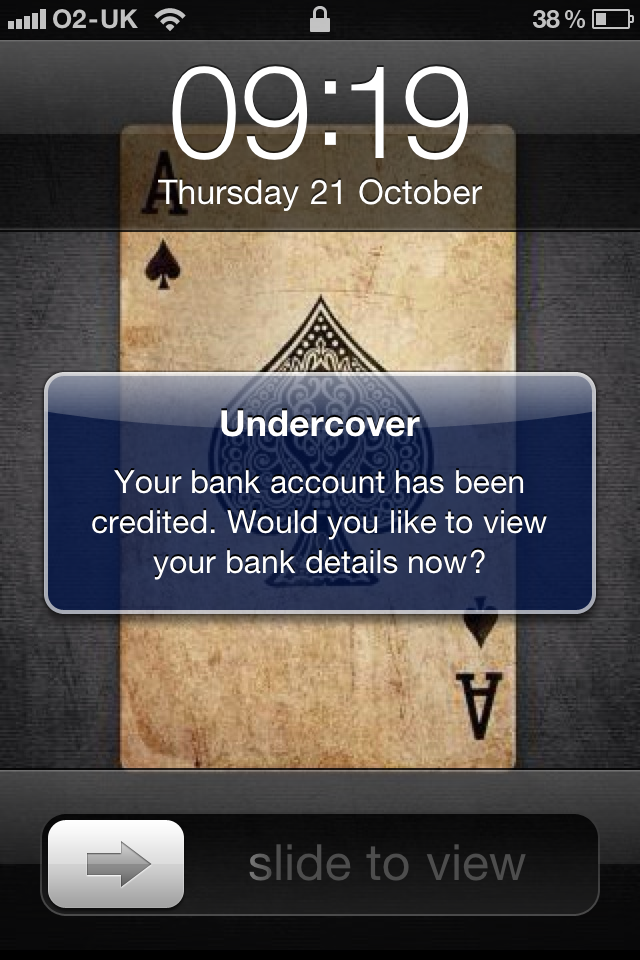
When the user goes and views this message, then a little game starts loading. In the background this is launching the Undercover App and sending the co-0rdinates. Personally I am not sure if there is value in this loading splash screen, perhaps it could do with being more stealthy and launch the app in the background. However I appreciate they want to ensure some time elapses whilst the information is sent.
So now as seen earlier when we log into the Undercover Dashboard we can see the co-ordinates, and it will continue to update its location whilst the application is running.
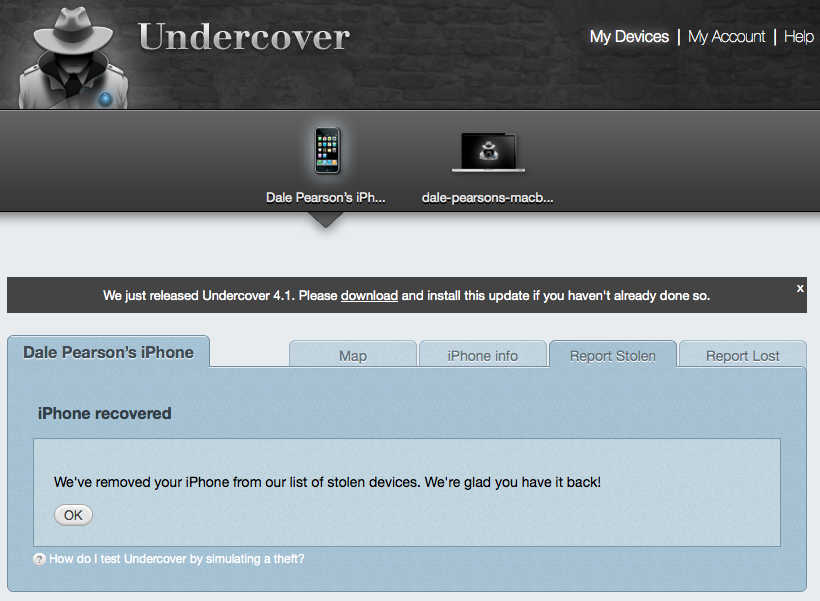
When the device has successfully sent it’s co-ordinates it sends you an email to confirm the device has been located.
Now we have finished playing with this we need to set our device as found.
So there we have the iPhone version, does a decent job of helping you find your lost or stolen device, although I would say the only negative is the requirement for device interaction (thief needs to read the notification), I am not sure if other offerings are fully automated. This solution also works on the iPod Touch and iPad.
So next we have the Mac OSX version, and I have to say I like this alot.
So as you would expect we need to install the application on our Mac, its just under 13Mb so not very big. Once the install has completed the machine will need to be rebooted to get Undercover up and running in the background. It will transfer its position again using the Skyhook Wireless Technology to give its position to around 10 meters.
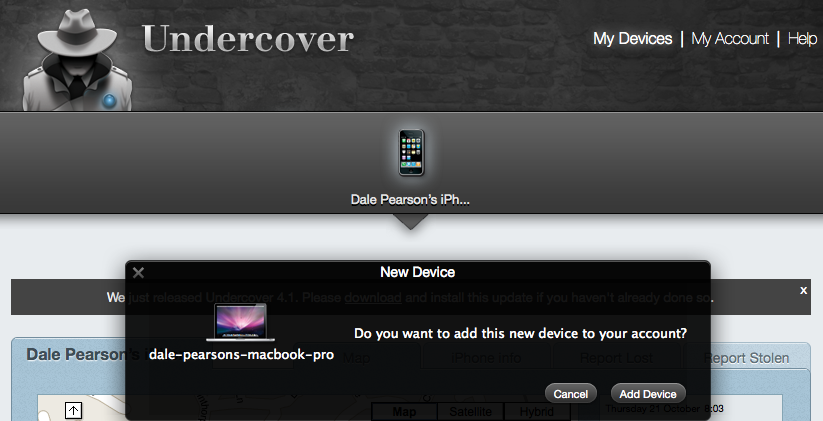
So as we have seen before we need to log into our Undercover dashboard and add and manage our new device.
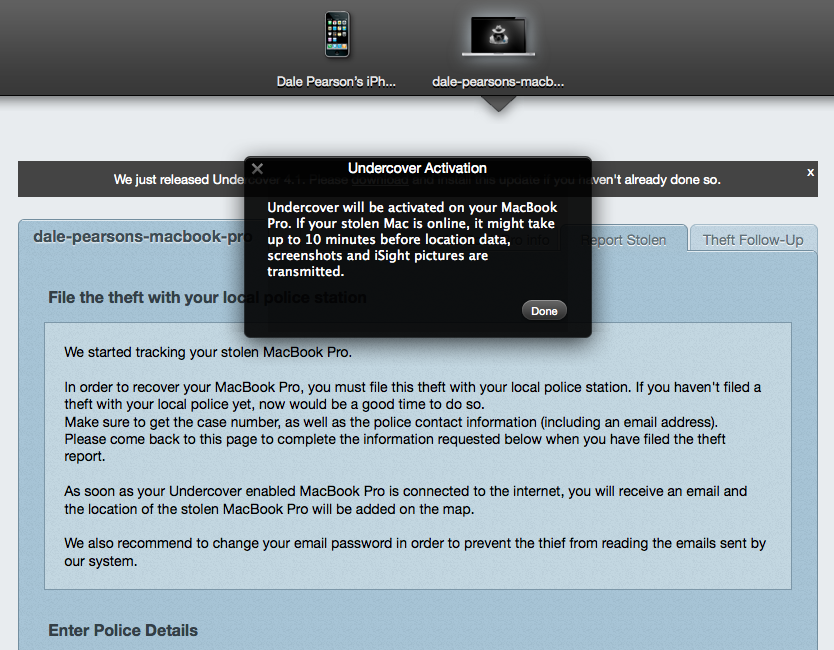
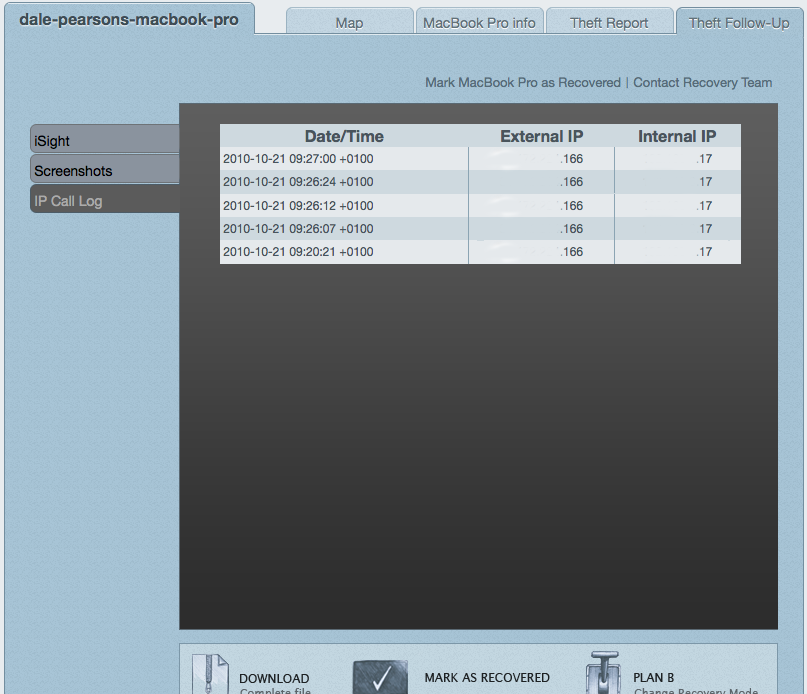
Now this time, when we mark our MBP as stolen, as default everything happens in a more stealthy fashion. As expected we get the map location we saw with our iPhone, but we also get details of IP address, we can then lookup the ISP being used, and other funky IP related antics.
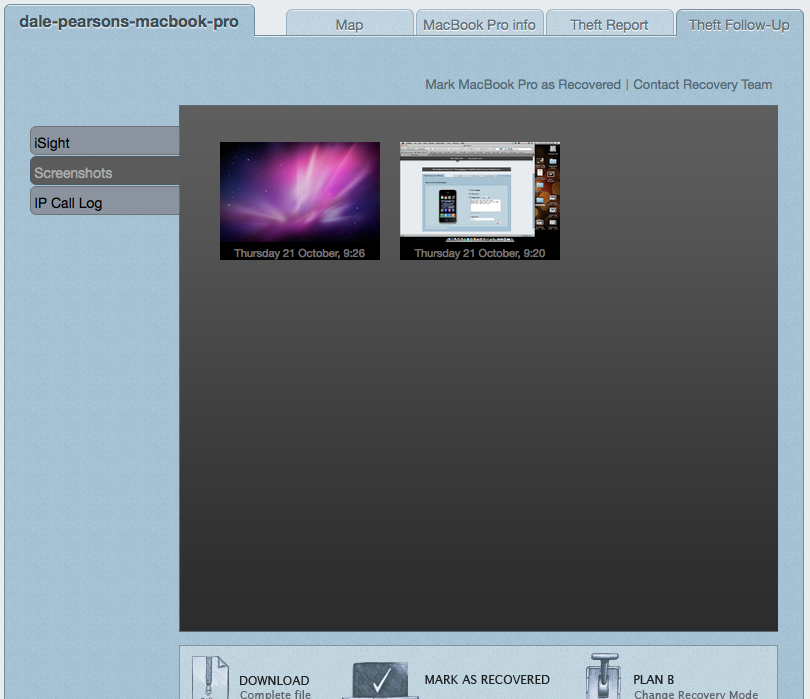
We can also get screenshots of what is being looked at at the time the information was collected.
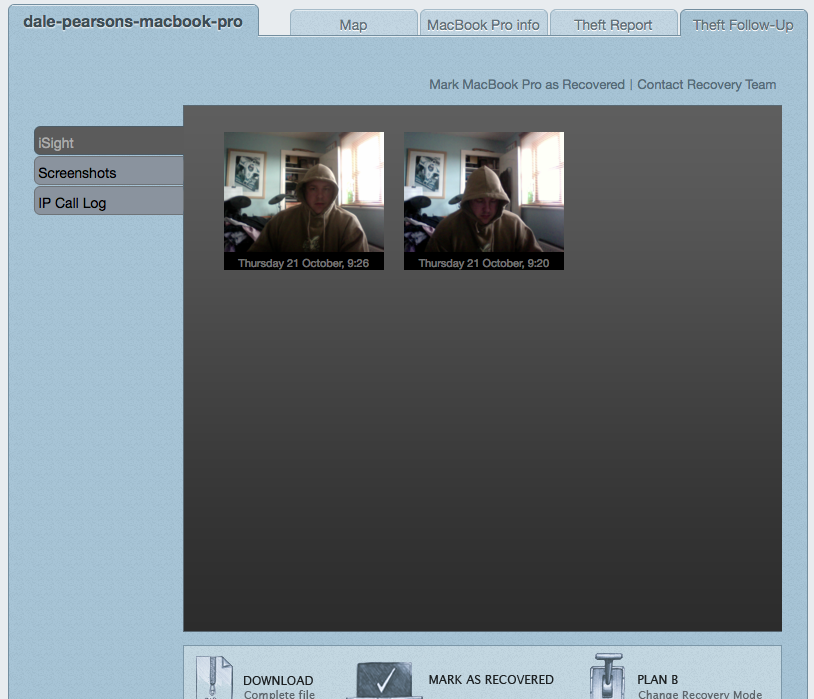
Then for the next trick, if the device is camera enabled, we can literally get a mug shot of the criminal using our device.
So now we can download all this information into a nice little bundle and send it off to our friendly law enforcement people, to recovery it for us 🙂 Its ok, there is a Plan B.
When we enter plan B mode we can move away from the stealth approach and fade the screen away so its very difficult to use, or we can simply blank the screen and have a customised message displayed on screen, making the machine unusable until restored, or formatted.
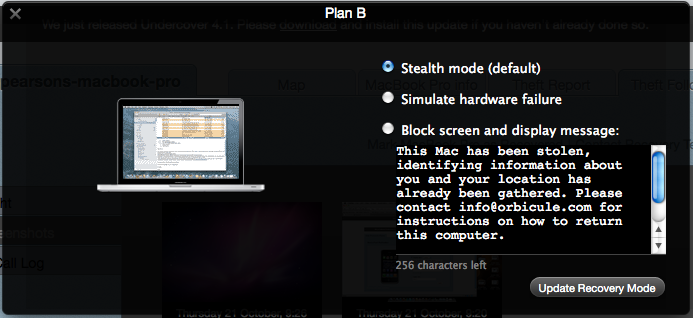
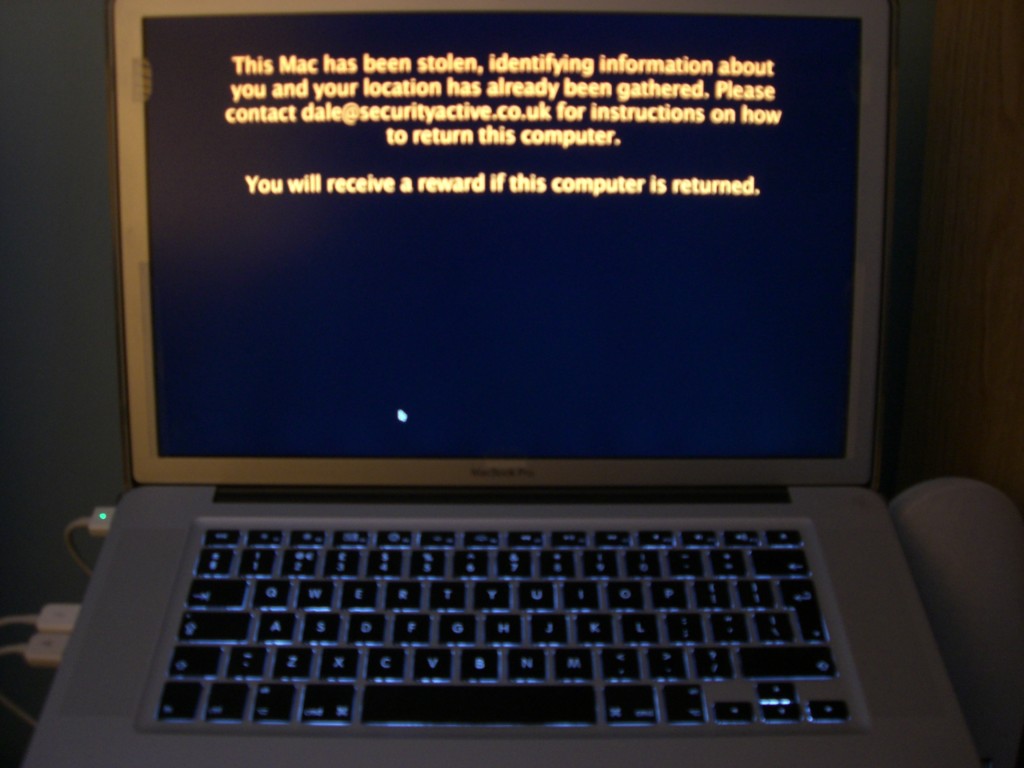
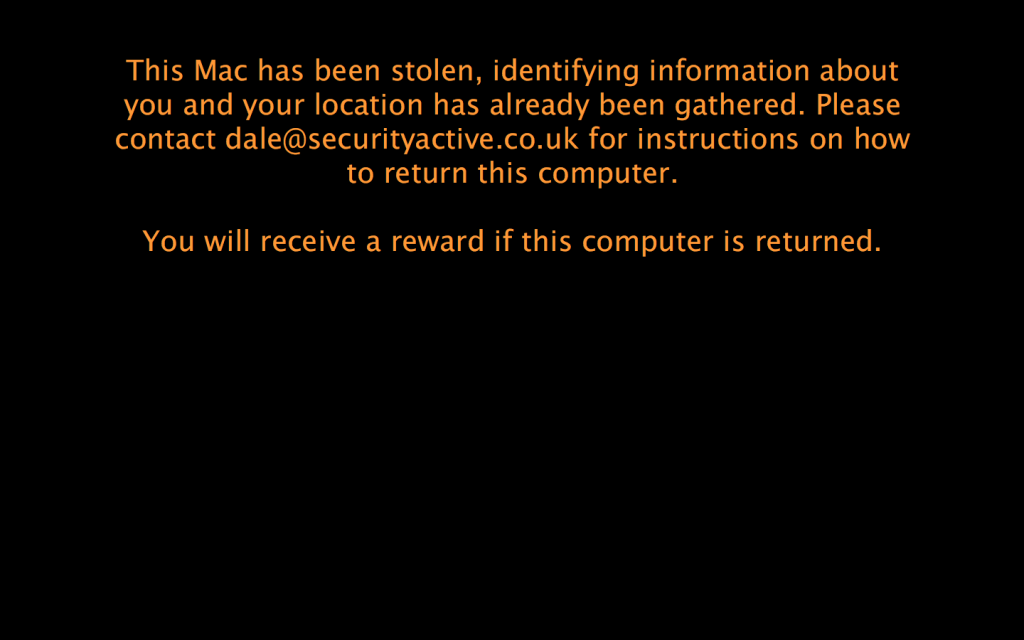
When this message is displayed, the computer also gives a little cry out for help via the speakers. Something along the lines of “Help, Help, Help, I am a stolen Macintosh Computer, please return me to my owner”
So on the whole I think this is a great product, and even more so as the price is so reasonable. For more information please check out the Orbicule site, and see some more information below on pricing etc.
Undercover Mac
Single User License £30.92 – Covers 1 Mac
Household License £37.23 – Covers up to 5 Macs
Site License £157.13 – Covers up to 25 Macs
Student License £24.61 – Proof of full-time student status will be required
Upgrade to Household £10.10 – Upgrades from a single user to a household license
Volume Education License £6.30 – When ordering 100 copies or more
Undercover iPhone / iPad
Covers all your iPhones and iPads £3.36