Elcomsoft are a Russian based software company, who make excellent security and audit products. Perhaps the name doesn’t ring a bell, but I am sure if you look at their product offerings you will be more than familiar with their products.
I first heard about Elcomsoft around 2002 I think it was when I needed to do some password recovery for some Office documents, and a colleague had a copy and it did its magic and we had a happy user. Ever since then I have kept the site bookmarked and keep a check on it every now and again.
Fast forward to 2010 and I find myself looking at iPhones and their suitability for use in the corporate world, and then I hear again about Elcomsoft releasing an iPhone Password Breaker (EPPB). So here we are, reviewing this product, and seeing just how it works and if it does what it says on the tin.
At the time of writing the professional version is advertised at £199 and the home version at £79. To see the difference between the version, please see the end of the review, or click here to visit the Elcomsoft site.
Thanks to the guys at Elcomsoft for letting me have a copy to review, and for helping resolving any issues I came across on the way.
So first things first, the EPPB requires a Windows Platform, so I fired up an XP SP3 VM, and a physical W7 box to do some GPU based testing.
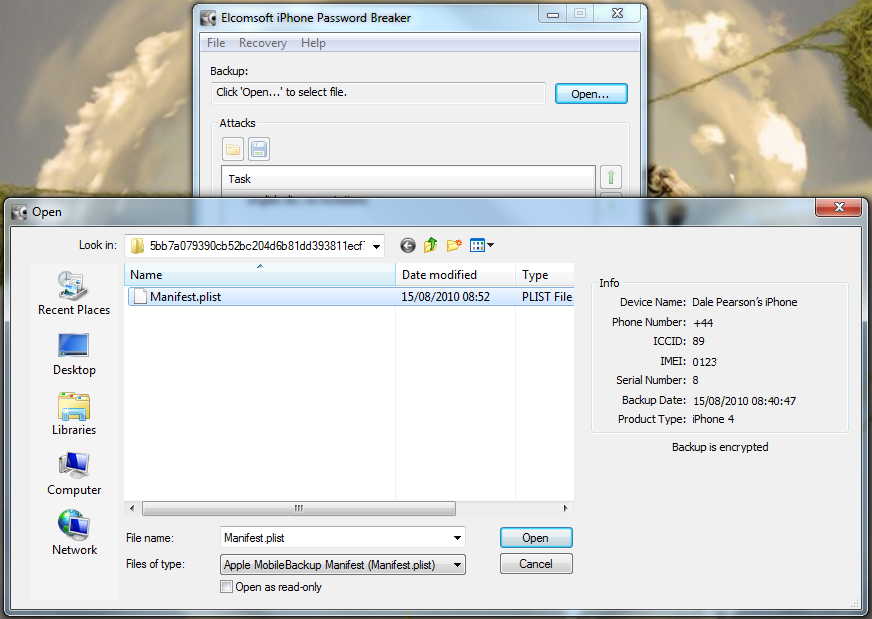
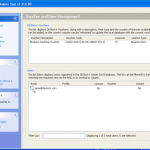
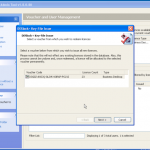
Once its installed we need to get hold of our encrypted iPhone backup. So the main file we are looking for is the Manifest.plist file, however if you will want to look at the keychain info you will want the complete contents of the appropriate folder.
When iTunes takes a backup of your iPhone it will include your settings files, from the preferences library, and databases, such as your calls, notes, bookmarks, password etc.
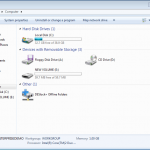
So if your on a Mac you need to look here > /Library/Application Support/MobileSync/Backup
On a PC you need to look here > Documents & Settings\\Application Data\Apple Computer\MobileSync\Backup or Users\\AppData\Roaming\Apple Computer\MobileSync\Backup
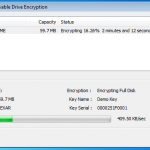
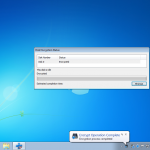
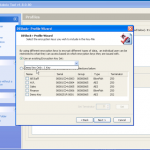
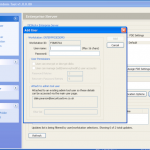
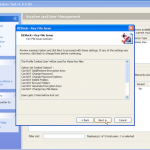
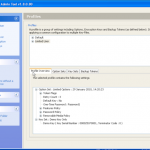
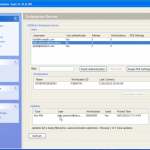
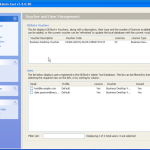
So once you have located your encrypted backup its time to fire up the password breaker and point it at the file in question. You will see the details of the device once you have selected it. We can see in this example the backup is that of an iPhone 4.
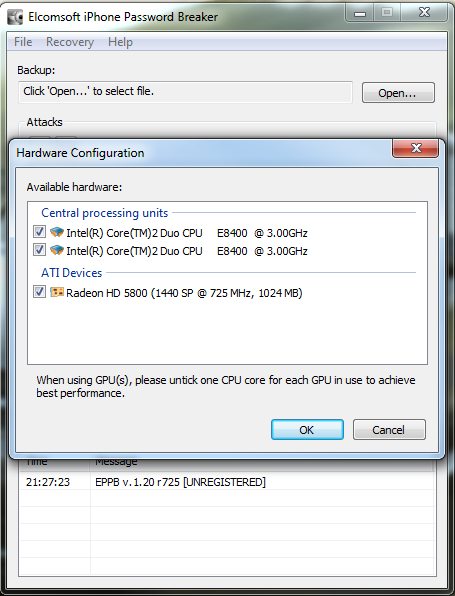
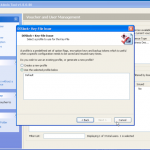
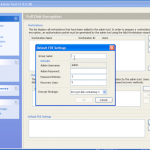
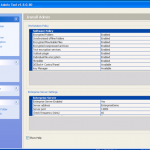
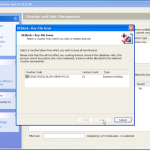
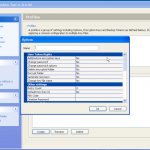
Now we have our file selected, lets make sure we are using the right hardware. So now we can enable / disable our CPU and GPU options.
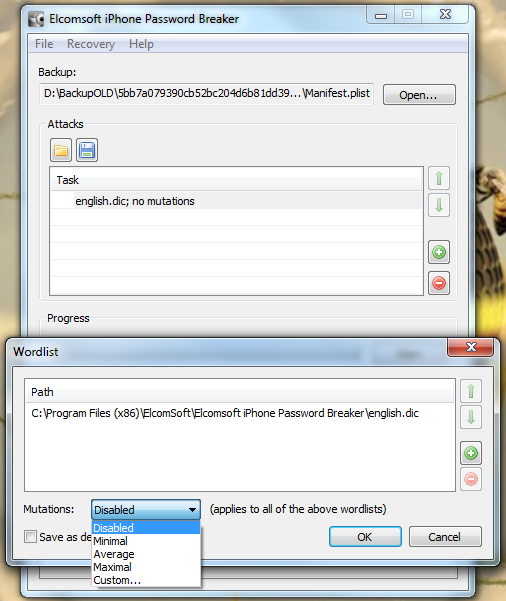
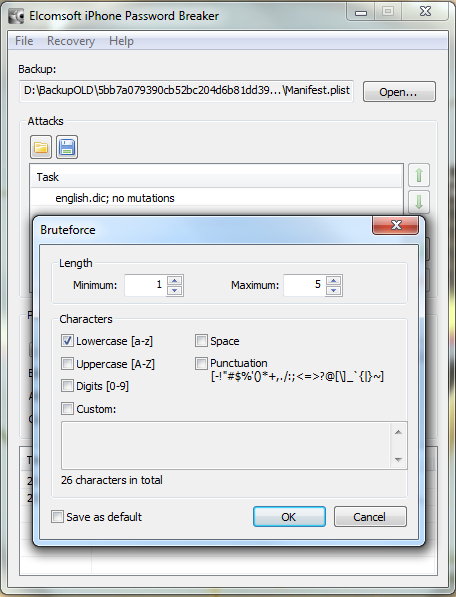
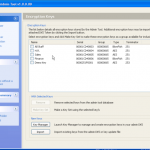
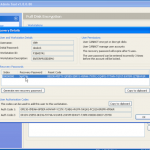
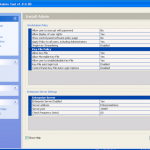
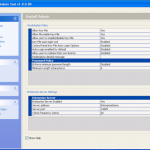
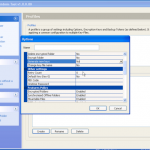
So now the hardware is selected, we are almost ready to get cracking 🙂 Now we just need to decide how we are going to go about it. We can use dictionary based attacks and supply files with the information (although it does come with some) or we can configure some brute force settings.
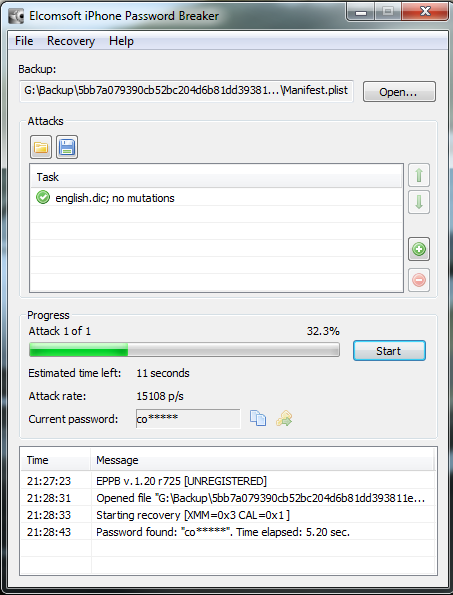
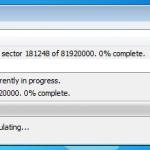
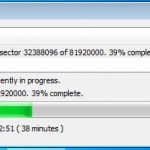
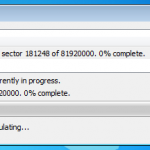
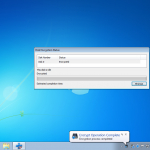
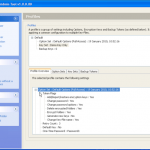
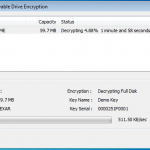
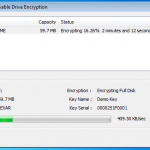
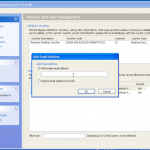
So now we are all configured, and lets face it, its all easy and straight forward. Now we kick off the cracking and watch the speed.
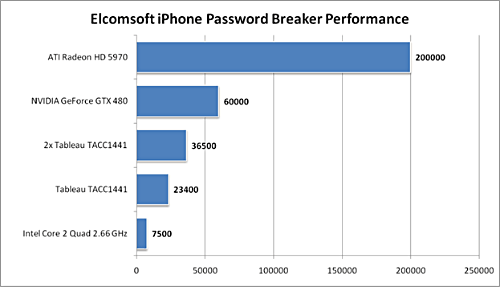
In the image below I am using a dual core Intel 3Ghz processor and a ATI Radeon 5880. As you can see its 15,108 passwords a second, not to shabby at all. My quickest crack was a 7 character dictionary password that was popped in 2.33 secs, GPU for the win. I also tried just a 64Bit Athlon 3Ghz on its own, and it only did 102 passwords a second, I also tried a 2.8Ghz Dual Core Intel in a VM and saw about 300 passwords a second, I then finally tried a cheaper GPU, a NVIDIA 8800 GTX and this provided the power to crunch 3,804 passwords a second.
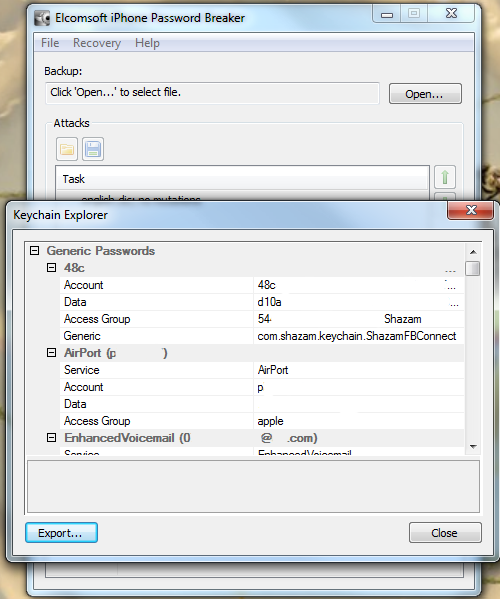
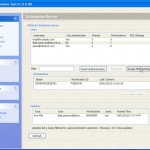
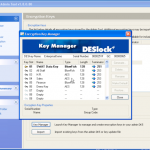
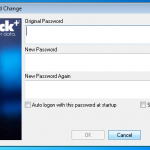
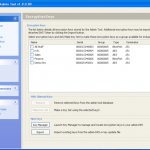
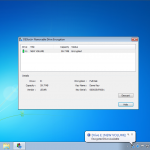
So now we have the password for this backup. We can now open the file in iTunes and complete a restore if we had forgotten the password. Or we can launch the keychain explorer and have a look at the information stored within the backup from the iPhone, as well as exporting the contents to an XML file.
Obviously I have sanitised the screen shot as it contains information I dont want to share, but you are going to see details of services used, usernames and passwords, access point information and access passwords, phone numbers and more.
So you may be thinking this is all good, but why is this tool of interest to me. Well first of all, as I have mentioned before many organisations are looking at, and are deploying iPhones. Out of the box they are not an enterprise ready tool and require 3rd party enterprise tools. So you get a call from you user, the iPhone needs restoring, they dont want to lose their information so they want to restore from the backup. Fine, however they have forgotten their password. So now you have an option to recover with this tool.
Next is the addition of gathering this information as part of a penetration test, or even a social engineering engagement. Obviously you need to get the files off the users machine, not the iPhone itself. I don’t need to tell you guys the ways this is possible. If your feeling really lazy, you may want to check file sharing networks, people share all sorts.
If you are a file sharing network user, please check you are not sharing your entire hard disk, and if you are…. STOP IT.
To conclude I think this is a tool worth having if your organisation is offering the use of iPhones, and it also has a place in your pentesting toolkit. For more information check out Elcomsofts website, and read below for some more information on the tool itself.
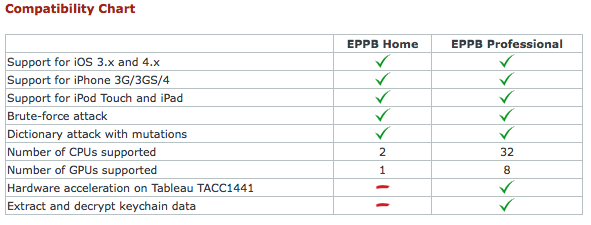
Elcomsoft iPhone Password Breaker enables forensic access to password-protected backups for iPhone, iPhone 3G, iPhone 3GS, iPhone 4, iPad, and iPod Touch 1st, 2nd, and 3rd Gen devices. Featuring the company’s patent-pending GPU acceleration technology, Elcomsoft iPhone Password Breaker is the first GPU-accelerated iPhone/iPod password recovery tool on the market. The new tool recovers the original plain-text password that protects encrypted backups containing address books, call logs, SMS archives, calendars, camera snapshots, voice mail and email account settings, applications, Web browsing history and cache. The program is also able to read and decrypt keychains (saved passwords to mail accounts, web sites and 3rd party applications) from password-protected backups (if password is known or recovered).
- Gain access to information stored in password-protected iPhone and iPod Touch backups
- Recover the original plain-text password
- Read and decrypt keychain data (email account passwords, Wi-Fi passwords, and passwords you enter into websites and some other applications)
- Save time with cost-efficient GPU acceleration when one or several ATI or NVIDIA video cards are installed
- Hardware acceleration on Tableau TACC1441 hardware
- Perform advanced dictionary attacks with highly customizable permutations
- Perform offline attacks without Apple iTunes installed
- Recover passwords to backups for original and ‘jailbroken’ iPhone, iPhone 3G, iPhone 3GS, iPhone 4, iPad, and iPod Touch 1st, 2nd, and 3rd Gen devices
- Compatible with all versions of iTunes (incl. 10.0) and iOS (3 and 4, incl. 4.1)
 Elcomsoft iPhone Password Breaker supports Windows XP, Windows Server 2003, Windows Server 2008, Windows Vista or Windows 7 with x32 and x64 architectures. Password-protected backups to iPhone, iPhone 3G, iPhone 3GS, iPhone 4, iPad, and iPod Touch 1st, 2nd, and 3rd Gen devices are supported.
Elcomsoft iPhone Password Breaker supports Windows XP, Windows Server 2003, Windows Server 2008, Windows Vista or Windows 7 with x32 and x64 architectures. Password-protected backups to iPhone, iPhone 3G, iPhone 3GS, iPhone 4, iPad, and iPod Touch 1st, 2nd, and 3rd Gen devices are supported.