So on the 27th April I boarded the train down to London and Earls Court to attend Infosecurity Europe 2010. I have not been for a few years, but I had heard good things from people that since moving to Earls Court there had been a big improvement, so I thought I would check it out.
So if you have not heard of this exhibition, here is a brief intro. Its been going for 15 years, there are around 300 vendors, along with keynote speeches, seminars and work shops, and with around 12,000 visitors it get busy. Basically its an event to speak to lots of vendors to find out what they are working on, and to see what’s of interest, as well as meet and network with alot of people, and sit down for some quick talks. Oh and don’t forget the freebies, lots of pens if your into pen testing 🙂
So what did I think of the event? I agree the location is better than previous so thats a good thing, however I feel the event lacked a common theme that I have been used to in the past. I am not sure if this is a good thing or bad really. For example in the past vendors would have been focusing on DLP or something, but this year it all just felt more like everyone was in their own silo, might be just me though.
I did get to meet some old faces, and met some new ones that I had only conversed with online, or who listen to the Eurotrash podcast so that was nice. I got to meet with some of the vendors I do some work with here and there, and some of the PR folks, and I hope to have some more interesting mini reviews coming along from the event.
So out of all these vendors who did I speak to, and was anything interesting going on. I went and listened to Ian Mann talk about social engineering (out of head hacker curiosity). Its only a 20 min talk, so not really alot of detail can be gained, but he gave a nice little overview of involving people at the target company, making them feel special, and the use of the fake get out of jail free card that I have mentioned myself. He did plug his book abit (I wont mention it here, you can find out for yourself) but I have not read it of received a review copy so cant comment on how good it is, and what answers it gives. Ian came across as a nice guy though.
I didnt really have much time between meeting with other vendors and people to attend any of the other talks, perhaps this is why others attend for all 3 days, I just dont have the free time to take 3 days out. I checked out the 3M stand who were giving a nice demo of a new micro projector, and a new version of their privacy screens for laptops and mobiles (more on this soon). I popped along to the Syngress stand and met Angelina for the first time, they had some good deals on their books and they seemed to be doing a good trade, I did miss Justin who was coming along to sign copies of his SQL book, another top infosec guy.
I met Steve Armstrong for the first time, some may know him from SANS (they had a stand there also), but he was at infosec to talk about Certified Digital Security which is a standard he has developed to provide a simple and easy to understand way for companies to get on the security trail. Its all freely available on the website, and if you want you can pay to become certified by an independant auditor, all sounds good to me.
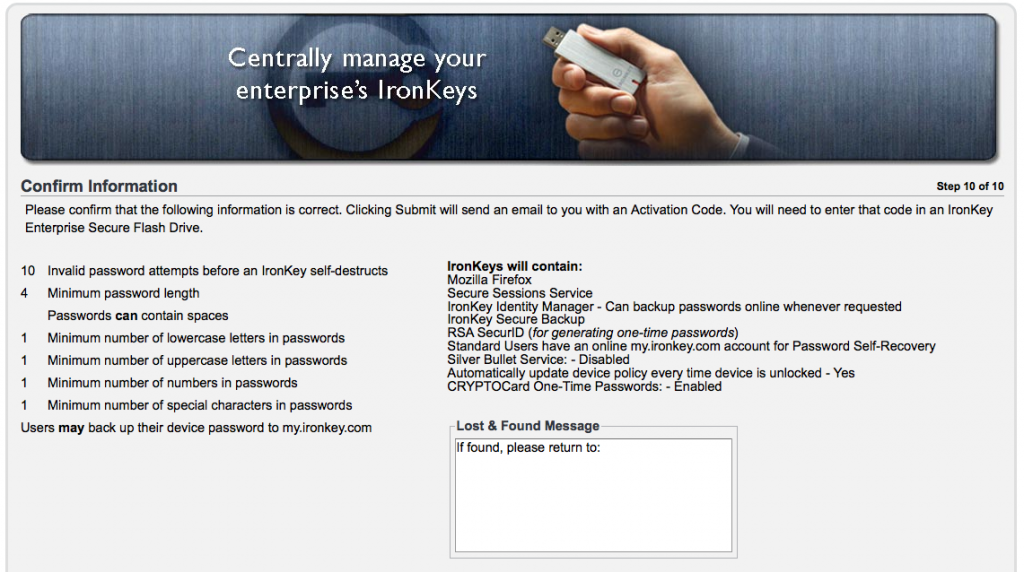
I met up with the guys at IronKey for a demonstration of their new online banking solution. Its essentially a restricted trusted platform that can be used for your banking and other secure online transactions. It creates an isolated browser environment, with a secure vpn connection to carry out your online transfers. In the demo it worked really well, bypassing keyloggers etc. They also talked to me about their OS on a stick, which does what is says on the tin really, a custom Linux or Windows OS running from your IronKey. I also asked about the D series of IronKeys as I have had some questions about that, and we discussed how the D series use cheaper memory and are a little slower than the S series IronKeys. With regards to all of this I hope to get review units to do some testing myself and share the results.
I also spoke to PGP, obviously as everyone is aware they are now under the ever growing Symantec umbrella. I am not sure how this will impact their offerings. MessageLabs where also at the show with their new Symantec branding, and I do know many people feel the MessageLabs offering and customer service has gone down hill a little since the acquisition, time will tell I guess.
I also popped along to the DESLock+ guys who had my review on the stand for people to take away, so thanks for that guys, and I also go to meet the lovely Annette Finch from C8 Consulting who does their PR.
I also spoke with SmoothWall, M86, Cisco, Blockmaster, DiskShred, MXI Security, SAINT and Webroot to name a few more. So all in all I had a good trip out, aside from missing my scheduled train home, so it really was a long day. So thanks to all the great people I spoke with and met, and to vendors where I got a couple of pens and some sweets 🙂