I am a probably a little biased, as I have been using a personal Ironkey 1GB S100 for some time now, and have recently got myself an 8GB S200 thanks to Don at The Ethical Hacker Network, so its clear I think they rock, and in my opinion I really do think they are the best secure USB Pen Drive on the market.
However I have never had any exposure to their enterprise offering, and with lots of companies now looking to adopt secure portable / removable media I think if Ironkey could be a good solution from a device perspective to help with data loss prevention. Ironkey have been kind enough to set me up with a temporary enterprise account, and sent me a couple of enterprise S200 1GB sticks to have a look how it all hangs together.
Before I get started, if you have never heard of Ironkey, let me just give you a little bit of info on what they are all about, and why in my opinion they are the 007 secure usb stick of choice, did I mention they look the business to 🙂
Enterprise Version Specs:
Rugged Metal Casing
Waterproof
Tamper-Resistant
AES 256BIT Hardware Encryption
FIPS Validated 140-2 Level 3
Strong Authentication
RSA SecureID / Verisign ID Protection
Secure Browser / Portable Apps
Self Destruction
Anti-Malware Protection
So on with the review. First we need an Ironkey Enterprise Account, and an Enterprise Ironkey, I was provided with both of these. When you get an Ironkey it comes in a little black box, once you have opened it up and plugged in the Enterprise Ironkey and the launcher is run, you are informed that you need to activate your Ironkey. (*Setup on a Mac)
 To progress past this stage you will need an activation code that your Ironkey Enterprise would have setup for you through the console. This will result in you having received an email with your activation code.
To progress past this stage you will need an activation code that your Ironkey Enterprise would have setup for you through the console. This will result in you having received an email with your activation code.
So with that in mind we will go to the Enterprise Web Interface and get things setup (policies, preferences and accounts).
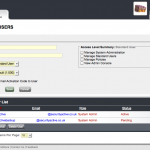
First we log in with our Enterprise Account number.
Now as its our first login we need to go through the 10 steps of getting our configuration setup that we are going to apply to all the Ironkeys in our enterprise.
Step 1 – Make sure we are the right man for the job…. Check 🙂
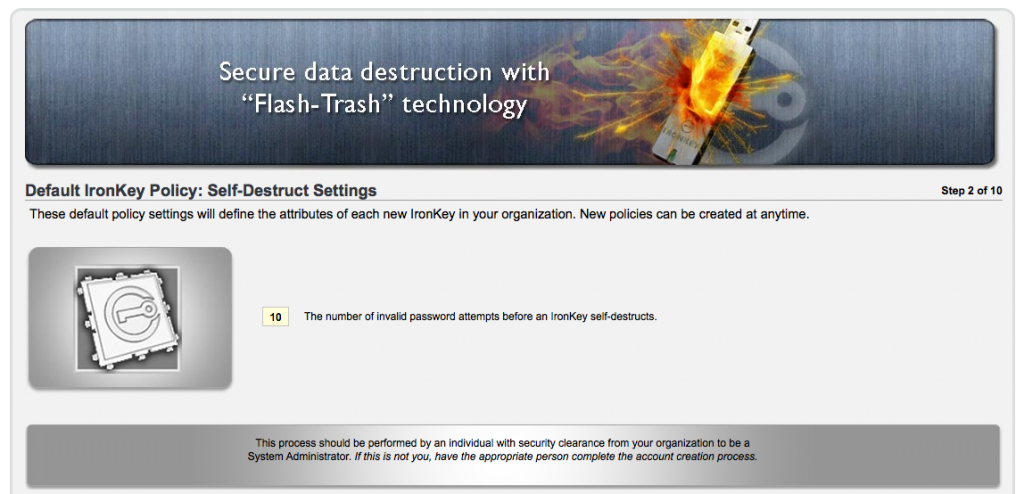
Step 2 – Now we need to define how many failed password attempts before the Ironkey self destructs. (Default is 10)
Its important to remember once destruction occurs, thats it. No undo or try again.
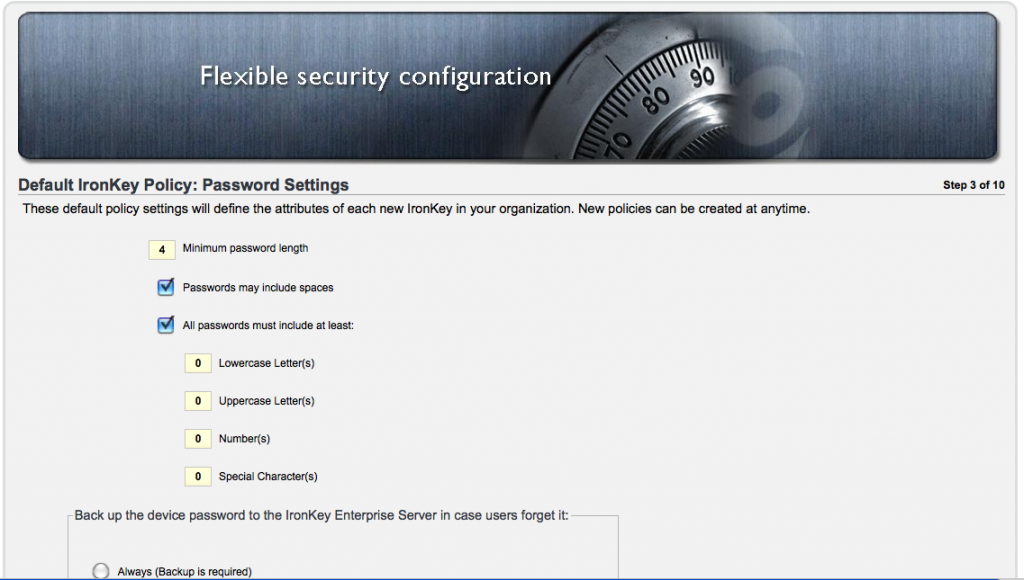
Step 3 – Now we define our password settings, complexity, and recovery settings.
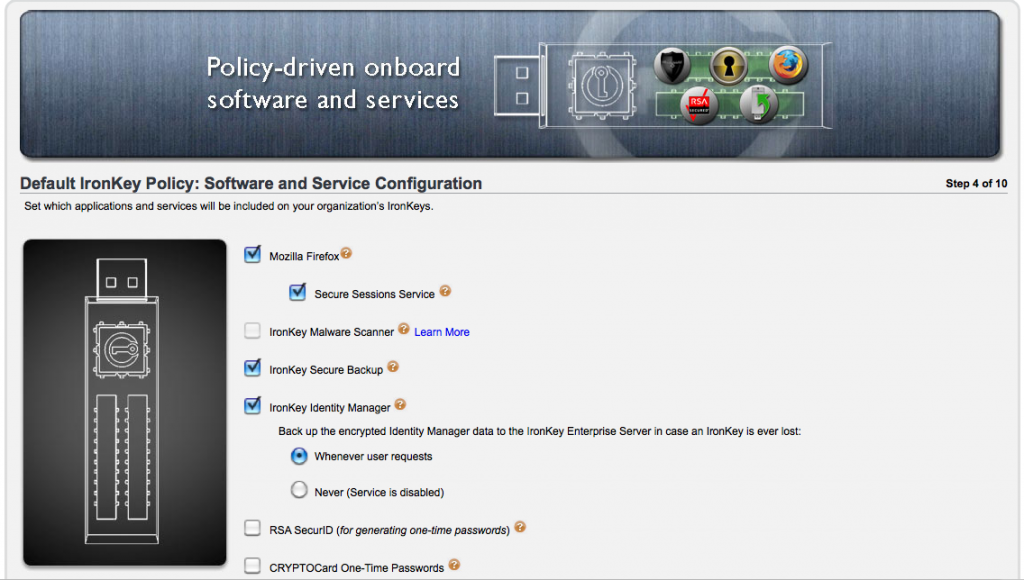
Step 4 – Now we setup the default applications available from the Ironkeys, Firefox, RSA, etc
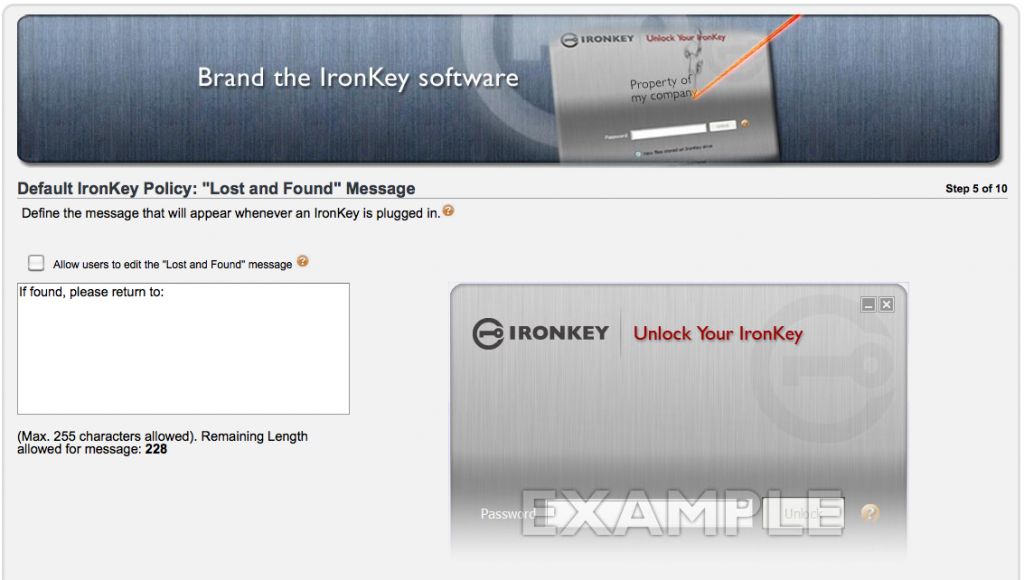
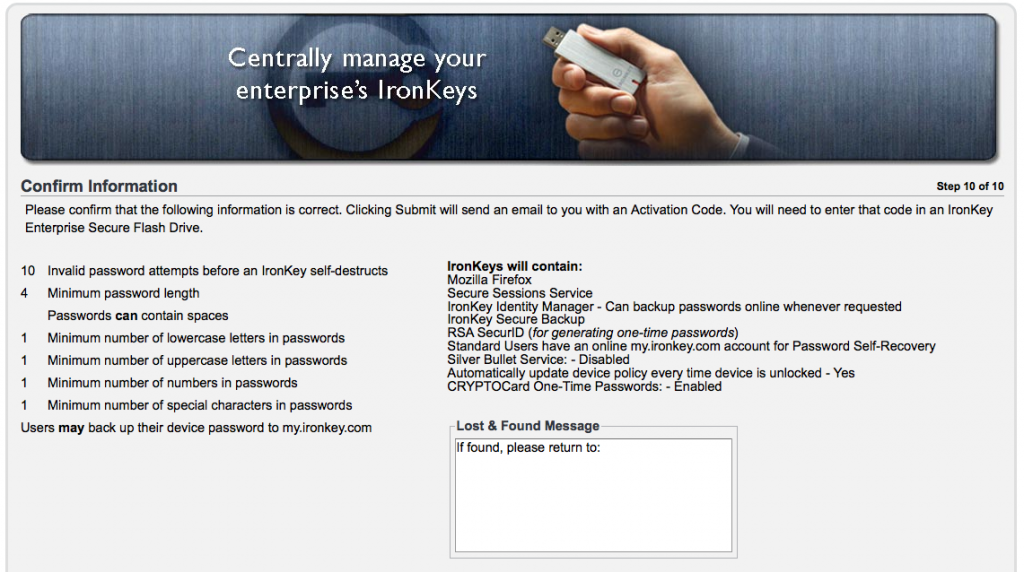
Step 5 – Its all about the Lost & Found. We can configure a message that will seen by anyone who inserts the Ironkey
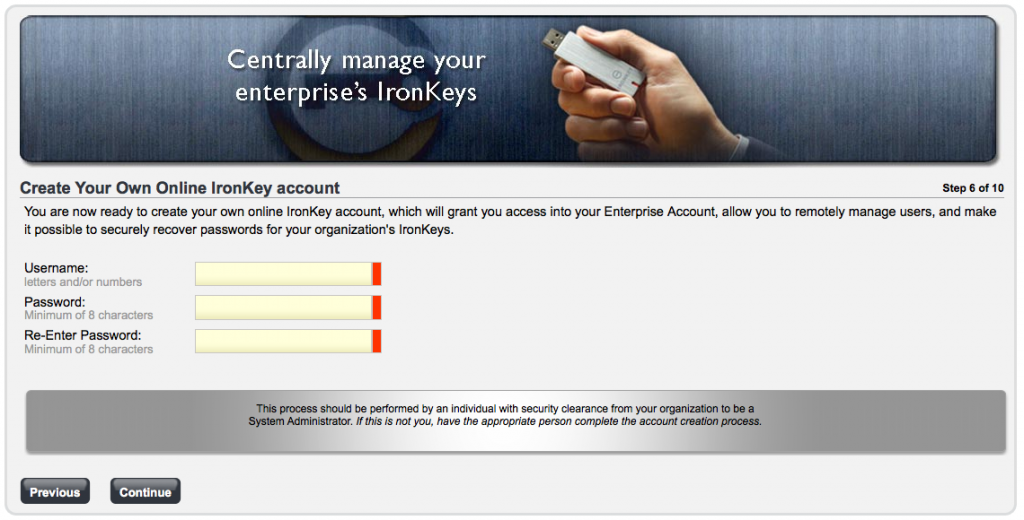
Step 6 – Now we setup the Enterprise Administrator Account, with a strong password.
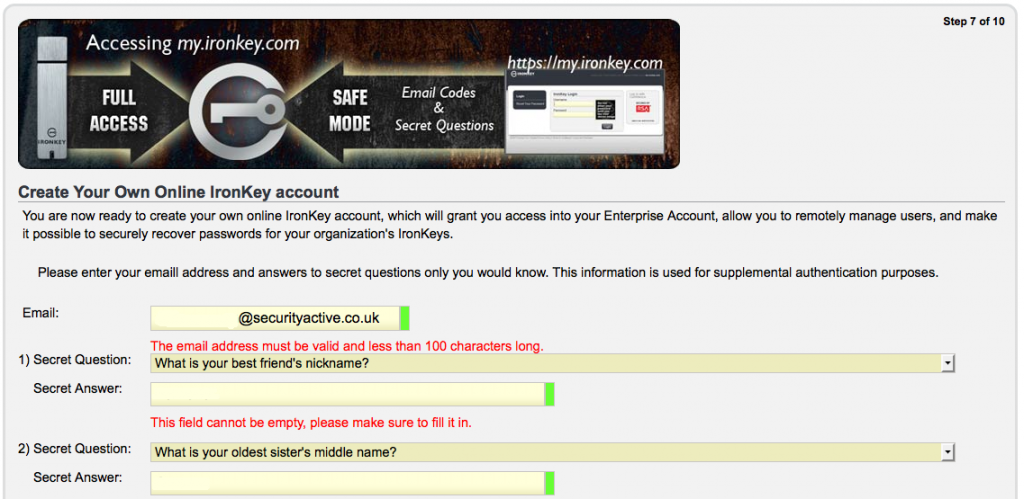
Step 7 – Time for some challenge response info, for when we forget ourselves.
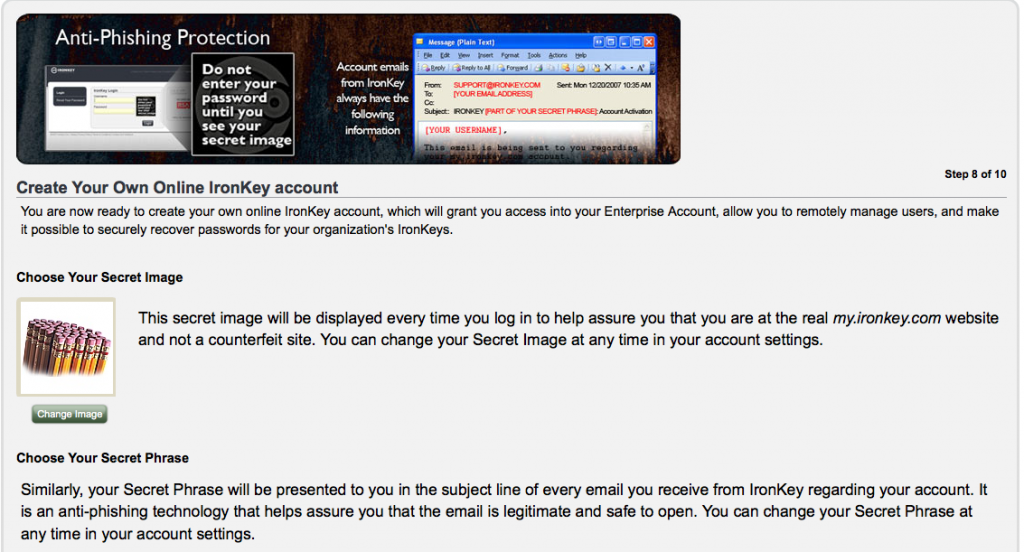
Step 8 – Now to create your secret identification image to ensure your at the REAL Ironkey admin page.
Step 9 – Creating your backup sys admin account.

Step 10 – Confirming everything is just how you wanted it.
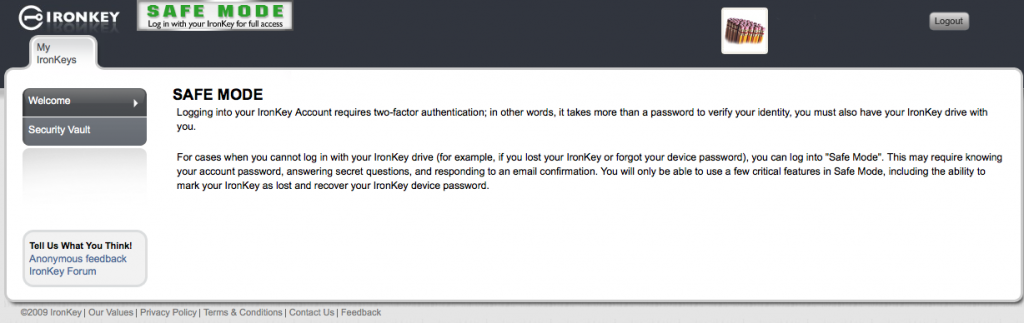
So now we have our admin account setup and our admin Ironkey associated. So lets take a look at what we can do at the web interface. Its important to understand that logging into your management interface requires two factor authentication, so not only your username and password, but your Ironkey also. If you dont have your Ironkey you just get into the Safe Mode option.
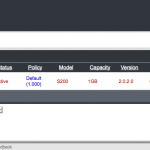
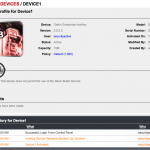
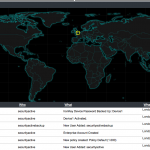
So when we login with the Ironkey we get all the good stuff, user management, policy creation alteration, alerts, log information and more. Things are pretty self explanatory, so here is a screen shot montage.
Now we can continue to activate our Ironkey, as we have created an account, and associate policy.
Now we setup a name for our Ironkey and a strong passphrase.

The key is then initialised and encrypted.

Then then if the user doesnt already have an online account, they are prompted to create one.

Now the user is good to go, the policy will have been applied, applications made available and secure storage created.
If the user is also an administrator they get access to admin tools from their Ironkey also, allowing them to recover data from other Ironkey, reauthorise, etc.

Below are also some screen shots of an Ironkey that has been assigned a Silver Bullet Policy meaning it cannot be used unless it is connected to the Internet for authentication, and a device that has been disabled.


Here is the control panel a user see’s on a Mac and PC, do control panel is currently available to Linux users.


Its pretty clear that PC users currently get better percs from the Ironkey, but regardless of the plaform your getting some awesome secure storage. I am really impressed with the simple yet appropriate level of control the Ironkey Enterprise solution gives, and I dont think I would hesitate to recommend this to a customer. I will say that I had one device get stuck in some sort of authentication loop, but Ironkey support where extremely helpful, and the few things we tried didn’t work so they sent out a replacement by Fedex.
Ironkey also offer pretty much the same offering but for personal users, and I will be putting up a similar mini review of this offering later in the month.
For more information on the Ironkey offerings, and to locate your local reseller visit the Ironkey website.
I will leave you with a short video clip I made, testing the waterproof theory of the Ironkey S200.
Waterproof Testing









 GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}


