The more we use computers, the more data we store on them. This data can be personal information, financial information, pictures of our family and friends, and more. However computers don’t last forever, and neither foes the hard disks we use to store our data on. This also includes our MP3 players, removable storage, digital cameras, etc.
I am sure you will have all seen the numerous stories in the media this year about camera’s, computers and hard disks being put up for sale on eBay only to find its got top secret military plans, or under cover spy information, customers financial records and pictures of things no one ever wanted to see. You may find this amazing, and often funny, but have you thought about your own data when you come to sell on your computer, give it to a friend or charity? Simple formatting and reinstalling the operating system is no guarantee your old data cant be recovered. You may also be responsible for hardware disposal at your organisation, perhaps you work in a government environment and are expected to remove all data from drives before disposal or selling.
The aim of this blog post is just to inform you about some of the opensource and commercial products that are available to help you securely erase your information, and reduce the risk of someone recovering your precious data.
Physical Destruction
Physical destruction of a hard disk is the most extreme method, but in some ways the most secure. Simply smashing up a hard disk with a hammer can be very effective and enjoyable  Just make sure you give it a good beating, as it is possible to restore the platters on occasion. The other method is to utilise the hard disk shredding facilities many companies offer, its not always cheap but it would make it a time consuming job to try and stick it all back together blue peter style. Finally degaussing is another method that can be used, this is passing a high powered magnet over the drive to scramble the data. Unlike the other methods a hard disk can sometimes be used after it has been degaussed.
Just make sure you give it a good beating, as it is possible to restore the platters on occasion. The other method is to utilise the hard disk shredding facilities many companies offer, its not always cheap but it would make it a time consuming job to try and stick it all back together blue peter style. Finally degaussing is another method that can be used, this is passing a high powered magnet over the drive to scramble the data. Unlike the other methods a hard disk can sometimes be used after it has been degaussed.



Software Destruction
The programs mentioned below offer logical options for securely erasing your data. This is achieved by multiple overwrites of random data. Depending on the level of guarantee you want you can select more or less overwrite passes, obviously this can be time consuming, so its a trade off. When dealing with military or government grade material, where physical destruction is not required there are specific defined requirements on the number of passes required, along with the type of data overwrite.
Secure Erase
Secure erase is built into the hard disk drive itself and thus is far less susceptible to malicious software attack than external software utilities.
The SE command is implemented in all ATA interface drives manufactured after 2001 (drives with capacities greater than 15 GB), according to testing by CMRR. Secure erase is a positive easy-to-use data destroy command, amounting to “electronic data shredding.†Executing the command causes a drive to internally completely erase all possible user data record areas by overwriting, including g-list records that could contain readable data in reallocated disk sectors (sectors that the drive no longer uses because they have hard errors).
SE is a simple addition to the existing “format drive†command present in computer operating systems and storage system software, and adds no cost to hard disk drives. Because the Secure Erase command is carried out within hard disk drives, no additional software is required either.
Eraser
Eraser is a nifty piece of software that you can use to do secure deletes of files from within your OS as well as securely overwriting the empty space on your drives. Eraser works with most version of Microsoft Windows and its an opensource product. It has various overwrite modes so there is something for everyone. I really like this tools, it does the job with no fuss.
DBAN
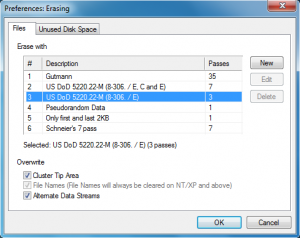
Darik’s Boot and Nuke is a self-contained boot disk that securely wipes the hard disks of most computers. DBAN will automatically and completely delete the contents of any hard disk that it can detect, which makes it an appropriate utility for bulk or emergency data destruction.
DBAN is a means of ensuring due diligence in computer recycling, a way of preventing identity theft if you want to sell a computer, and a good way to totally clean a Microsoft Windows installation of viruses and spyware. DBAN prevents or thoroughly hinders all known techniques of hard disk forensic analysis. DBAN is a free software product that can be used at home or in a business at zero cost.
I have been using this for a long time now, both at home and at work. You may be familiar with it if your a user of the Ultimate Boot CD.
Wipe Drive Pro
Wipe Drive Pro is a commercial product used by many government organisations to securely erase hard disks and over removable media. There is a demo available, but the product itself costs about $100. I have personally not used this product myself, but is an option for you to look into.
BC Wipe
BC Wipe is a commercial product used by many government and defense agencies. BC Wipe enables you to permanently erase files so that they can never be recovered or undeleted. BCWipe embeds itself within Windows and can be activated from the Explorer FILE Menu OR from the context (right click) menu OR from a command-line prompt. BCWipe complies with both the U.S. Department of Defense (DoD 5220.22-M) standard or the Peter Gutmann wiping schemes, either of which can be invoked from within the product. You can also create and use your own customized wiping scheme to wipe sensitive information from storage devices installed on your computer. BC Wipe has offerings for Windows, Mac and Linux, and costs around $40.
Blancco
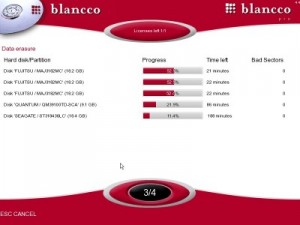
Blancco like the other tools is again a commercial product used by many government organisations to securely erase data from hard disks. Permanently erase data to prevent data recovery from unwanted sources, use a data shredder product such as Blancco File Shredder for day-to-day needs, or get IT asset management software to control, redeploy or resell your company’s IT assets. Blancco’s products and services are for professional use, often referred to as ‘enterprise grade’ and offer data erasure, reporting and auditing. Blancco starts at about £22 for the standard edition, and currently is only available for Windows.
IBAS Expert Eraser
ExpertEraser is a program that runs from your floppy drive, allowing your entire hard disk to be overwritten securely. It can run on any computer that can boot to DOS from a floppy diskette / CDROM, regardless of how the drive was formatted. The program exceeds US DoD standard 5220.22-M. The purpose of ExpertEraser is to remove all traces of information from a hard drive. By utilising cutting edge erasure technology, ExpertEraser provides users with an efficient tool for removing all traces of data from hard drive slated for disposal, recycling or reuse.
KROLL Ontrack Eraser
Ontrack Eraser software is an easy-to-use, highly flexible data erasure tool that erases all traces of data stored on a targeted media – ensuring that sensitive information does not fall into the wrong hands. Ontrack Eraser has been approved by the CESG to the highest HMG Infosec 5 standards.














