Last year (2009) I got a call about reviewing a Full Disk Encryption product called DESlock+. I had not heard of the product, so a quick search later and more information was revealed. As encryption is an import consideration for users at home and within an organisation, and I had been looking at a few vendors for my day job I thought it would be some time well spent, and may be of use to some of you guys.
DESlock+ Enterprise is the product I am going to be look at, and its made by a company called DES. DES were founded in 1985, and the companies systems and methods originated within the British Government Communications Headquarters. The original users of DES products were government based, but over time have spread into other sectors. Over the past twelve years DES has also marketed the DESkey and DESlock range of software protection products. With an estimated 500,000 units in use throughout the world to date, sales of the DESkey continue to grow.

- Full Disk Encryption
- Removable Media Encryption
- Encrypt Email, folders and files
- Multiple encryption keys stored in a keyfile
- AES, 3DES, Blowfish Algorithms
- Encrypted mountable files
- Secure data shredder
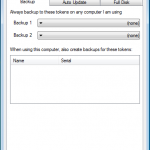
- Keyfile backup utility
- Scalable centralised licence and key management
- Remote keyfile distribution
- Software feature policy control
- Includes DESkey USB manager tokens

When reviewing encryption products its can often be a difficult task. Lets face it the most important thing an encryption product can do is encrypt, if it doesn’t do that then we are in a pretty bad situation. So you will be happy to hear DESlock+ does encrypt and it works in a no nonsense way so with that in mind we are off to an excellent start.
To speed up my review Jamie Gordon (excellent guy) sent me a Windows 7 Virtual Machine with the DESlock product pre-installed, as like everyone getting the time to have a look at a product can be difficult. So the starting situation is essentially this. We have a Windows 7 client machine that has DESlock+ installed, and connecting back to DES HQ. The client gets its policy applied when we start up and authenticate for the first time, and we have various options available to us, but the Full Disk encryption has not yet been applied, our friend Jamie takes care of that for us remotely later.
I have a hell of alot of screenshot, about 120 or so, obviously I don’t want to post all of these, so as part of this review I will give an overview of whats going on, various configuration and functional options. I can tell you now the best thing for me about DESlock+ is it does what it says on the tin, with no fuss, and you don’t need to be a rocket scientist to configure your policy and get it up and running. I will basically show the shredder options, encrypting individual files, removable media and of course full disk encryption.
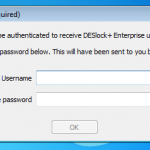
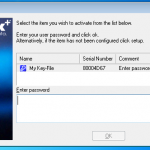
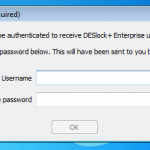
So to get things started we boot up our VM. Its important to remember that normally in an enterprise environment you would normally be logging onto a domain, however in this example this is not the case. So any credentials are not resolved from my domain credentials, its needs to be done manually. So I need to authenticate myself with the DESlock+ Enterprise Server using a one time password to get things started.

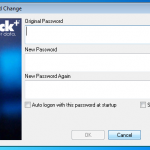
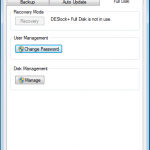
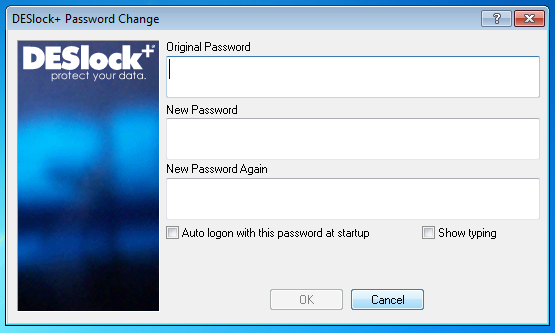
Once authenticated we need to change the password.

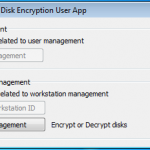
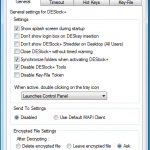
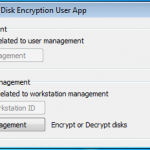
So now we are presented with the Desktop to go about our daily duties. Its worth noting we have the features of DESlock+ available to us now, but we have not yet had our hard disk encrypted.

So everything looks as normal, although we have the DESlock+ Shredder, and a couple of new icons in the task bar.



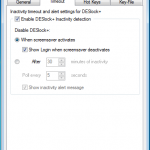
I will add a picture montage at the end of this review that shows various screen shots, so if you want to know what happens when you look further at these properties you can check them out.
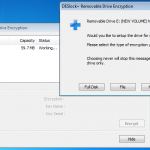
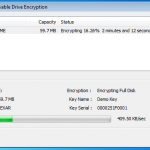
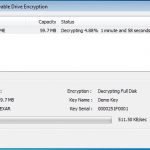
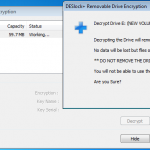
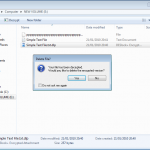
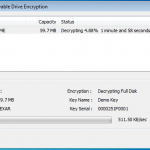
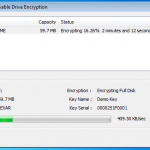
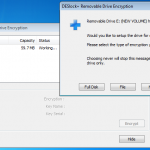
So lets see what happens when I plug in a USB stick (A Dell branded 64Mb in this case). DESlock+ detects the USB device and prompts to do its thing.

So lets kick off the removable device encryption.



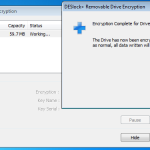
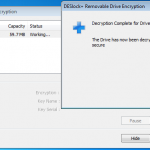
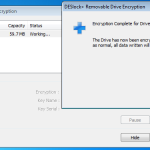
Encryption Completed.

Once the drive was encrypted a put a couple of files on there, ejected the drive and tried the stick on a windows machine, linux and Mac. All found the drive to be unreadable, so no chance at getting at that data. So good stuff.
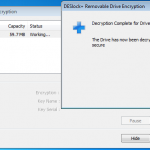
So next I decided to decrypt the drive, and then try just encrypting a single file.



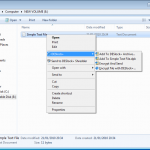
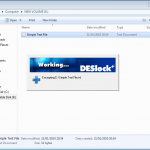
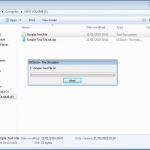
So now we create a file, and right click for our encryption options.


Once the file is encrypted the remainder of the stick was still usable, but as expected the encrypted file is not accessible. Obviously files can be encrypted like this locally, as well as on removable media. This allows for some versatile application, whilst ensuring control and protection over your data.
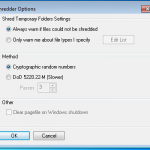
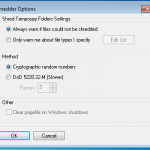
Of course for that little bit of additional protection its a good idea to securely erase files when your done with them, and this brings us along to the DESlock+ Shredder. You can choose how many passes you want to make when erasing the data, and choose between two methods.


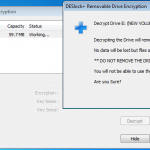
So we know we can encrypt our files as needed, and we can securely erase them also. So the next thing to get sorted is obviously full disk encryption.
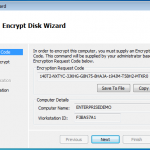
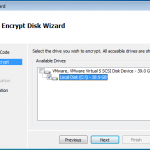
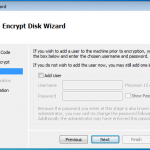
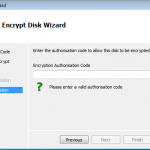
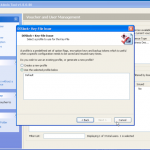
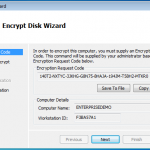
There is an option to encrypt using a local wizard, and an activation code you get from the administrator. I did have a look at this option as the screen shots below show. However I decided to go the remote route as this is an enterprise offering, and see how it works from the admin console.





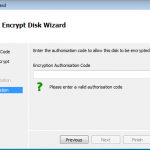
 As you can see above. If we had an authorisation code from our admin, we could kick off the full disk encryption ourselves.
As you can see above. If we had an authorisation code from our admin, we could kick off the full disk encryption ourselves.
So now lets take a brief look at what we see as an administrator from the DESlock+ Enterprise console.

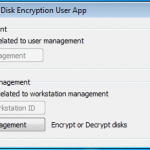
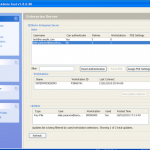
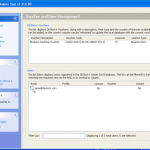
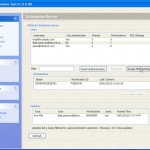
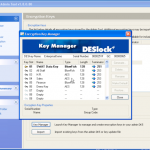
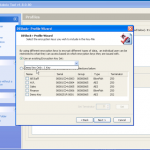
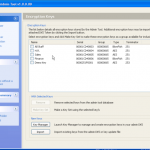
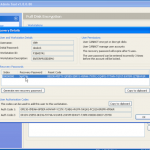
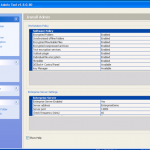
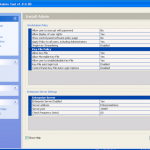
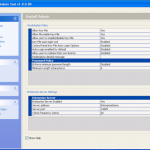
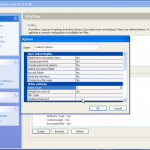
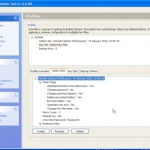
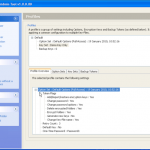
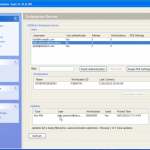
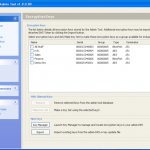
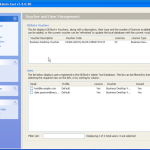
Once we are in the admin console we have access to the various configuration options. We have the ability manage both DESlock vouchers (these control what you can or cant do based on what you have purchased) and users of the system. From a day to day perspective this is probably where you will spend time verifying what accounts are created, active machines and so forth when your first getting set up. Then there is the profiles section, this does what it says on the tin. It allows the for creation, modification and assigning of encryption profiles. Next is the Enterprise server section, this shows the user details and associated machine, when they last connected, keyfiles in use etc. The full disk encryption section is fairly obvious, this where you manage the FDE of machines in your environment. We then have the encryption keys section, this is a useful section as you can create multiple encryption keys for different parts of your organisation, to give extra levels of control. Finally the install admin section, this pulls various information together to form a registry key that is applied as part of the product install on client machines.
I viewed this section remotely with the DES guys, so I didn’t have time to have a proper play myself, but I did take some snapshots that you can see towards the end of the review.
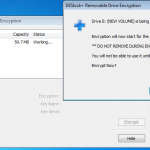
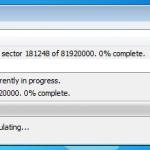
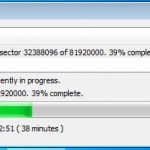
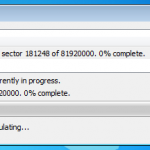
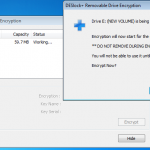
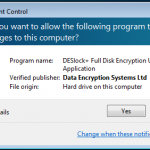
So whilst viewing remotely, Jamie kicked off my remote encryption of my VM machine. It worked a charm with no fuss. My machine connected with the remote server, downloaded configuration updates, and then started encrypting. I even rebooted mid encryption as a test and it resumed once logged in.
So here are a couple of snaps to show what’s going on at the client end.







Now lets reboot.

Job Done 🙂
Wrap up and thoughts….
So we have gone through the motions, seen some screen shots, but is it actually any good. Personally yes I think it is. For me when it comes to encryption products it can be a difficult evaluation process, because lets face it if its encrypting our data in a secure method its ticking the box. I think what makes DESlock+ a good product is that its simple. I don’t mean that in a negative way at all, the product does what it says on the tin. It encrypts files, removable media, full disk encryption as well as emails and other bits and bobs I was not able to spend time in testing, and it does it in a professional no fuss approach. The menus and clear and simple to understand, policy configuration is easy and flexible, I like the fact you can use different encryption keys in different parts of the business, and for different users, this gives an extra level of access control. I like how easy it is to revoke access to encrypted files and devices in the event of loss, and I like the challenge response stuff for when people forget passwords and I like the secure deletion with the shredder.
I would certainly make organisations (especially SME’s) I work with aware of DESlock+ as well considering their similar home offering to family and friends who just want to encrypt files and don’t need FDE. However as with everything I had a few gripes with the product whilst reviewing. Its great that you can encrypt removable media, but its abit frustrating you cant share the content with non DESlock+ customers (they now have an offering for this coming soon), and I have seen some other products that allow custom configuration messages for users screens, this isn’t a major one for me but its a bonus sometimes. Lastly its my understanding that the product itself does not support distribution across the organisation, so you need to utilise some other tooling to package up and distribute DESlock+. None of this stops me thinking its a good tool, just sharing my thoughts. It is also worth noting the DESlock+ products only work on W2K upwards, so no support for Linux and OSX.
Since I have completed the review DESlock+ has been FIPS 140-2 validated, so congratulations and well done to the guys on that achievement. They have also made a product available called DESlock Reader which will allow non DES customers to decrypt emails, and files that have been encrypted with DESlock+ (obviously you will need to know a pre shared password to decrypt), this something that can be enabled or disabled at a policy level if you don’t want everyone having the ability to potentially share data outside the organisation. Another product is in the pipeline that should be out later this month, and this is DESlock+ Go. This product is all about encrypting removable media to share with 3rd parties in a secure manner. The 3rd party doesn’t need to install any software, it all runs from the encrypted package, and if its writable media such as a USB device, the 3rd party can even write data back to the device to share securely back with the original DES user. Finally they also have an MSI configuration in the pipeline that I think will help with the installation and distribution of the product, especially in larger enterprises.
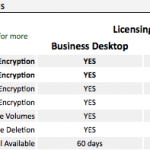
For pricing your best of contacting DES yourself, but its my understanding the Home versions are about £45, which just provides secure file encryption (not FDE). Business Desktop licences start at around £75 for small numbers of licences and then decrease in cost as the number of users increases over 1000, and the Enterprise Server is about £250. Maintenance is also available at additional cost as needed.
Picture Montage